Introduction
Linux has a unique way of implementing some network protocols, especially tunneling protocols, as virtual network interfaces. This approach provides a unified way to configure and test various protocols using standard Linux networking tools.
In this post, we’ll explore this concept and show how to use these interfaces with Ostinato to test various protocols that are not natively supported by Ostinato.
Understanding Linux Virtual Network Interfaces
In Linux, many network protocols are implemented as virtual network interfaces rather than just protocol stacks. This means protocols like MACsec, IPsec, VXLAN, and others appear as regular network interfaces in the system. You can configure them using the standard ip command with protocol specific parameters.
This approach offers several advantages for network testing.
- Protocols appear as standard Linux network interfaces
- Use existing Linux networking commands
- Easy integration with other networking features
- Test protocols in a more realistic environment
Here are some of the protocols implemented as virtual interfaces in the Linux kernel (Run man ip-link and look for the allowed values for the type param to see the full list) -
- Tunneling Protocols
- IPIP - IP-in-IP tunneling
- SIT - IPv6-in-IPv4 tunneling
- GRE - Generic Routing Encapsulation
- VXLAN - Virtual Extensible LAN
- GTP - GPRS Tunneling Protocol
- Geneve - Generic Network Virtualization Encapsulation
- Security Protocols
- MACsec (802.1AE) - MAC-layer security
- Container/Virtualization Networking
- IPVLAN - Lightweight L2 container networking
- MACVLAN - Multiple MAC addresses on single interface
- VETH - Virtual Ethernet pairs
- TAP/TUN - Virtual network devices
- Industrial Protocols
- HSR/PRP - High-availability Seamless Redundancy/Parallel Redundancy Protocol
- Bridging and Aggregation
- Bridge - Network bridging
- Bonding - Link aggregation
- VLAN - Virtual LAN interface
- Special Purpose
- Dummy - Dummy network interface
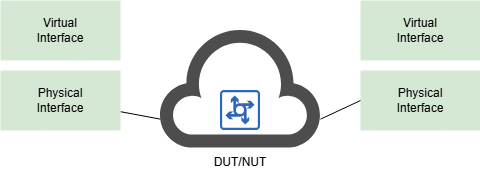
Since these are virtual interfaces, they are typically ‘stacked’ on top of a physical interface. For example, a MACsec interface is typically stacked on top of a physical interface like eth0.
Depending on the protocol, the virtual interface may either be an ethernet interface (e.g. macsec) or an IP interface (e.g. GTP).
The tunneling and security protocols also typically have a similar peer. The peer would be stacked similarly if it is running Linux or can be a vendor device with their own proprietary protocol stack.
How to use Virtual Network Interfaces with Ostinato
Since the virtual interfaces are standard Linux interfaces, Ostinato will list them in its port list. Both the virtual interface and the physical interface would appear in Ostinato’s port list.

You MUST configure traffic streams on the virtual interface (NOT the physical interface).
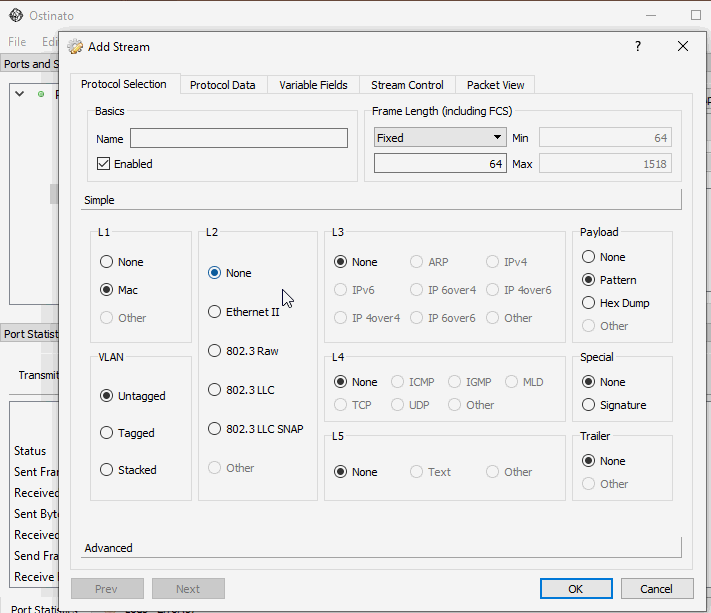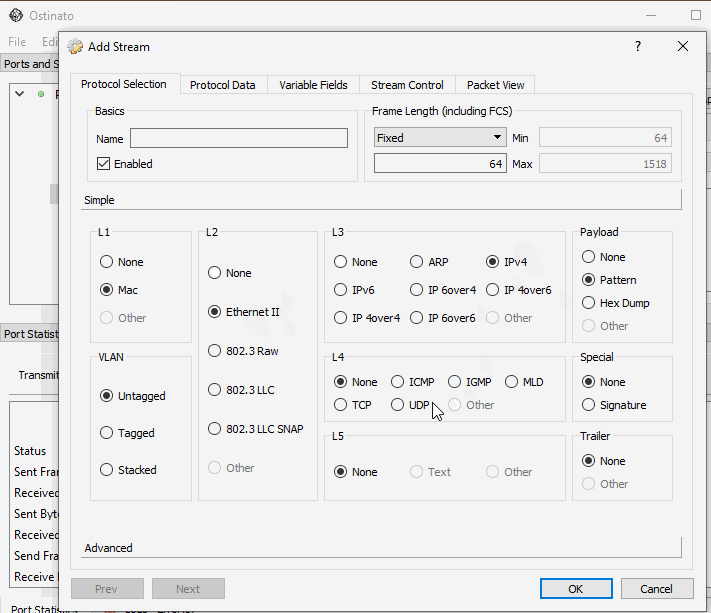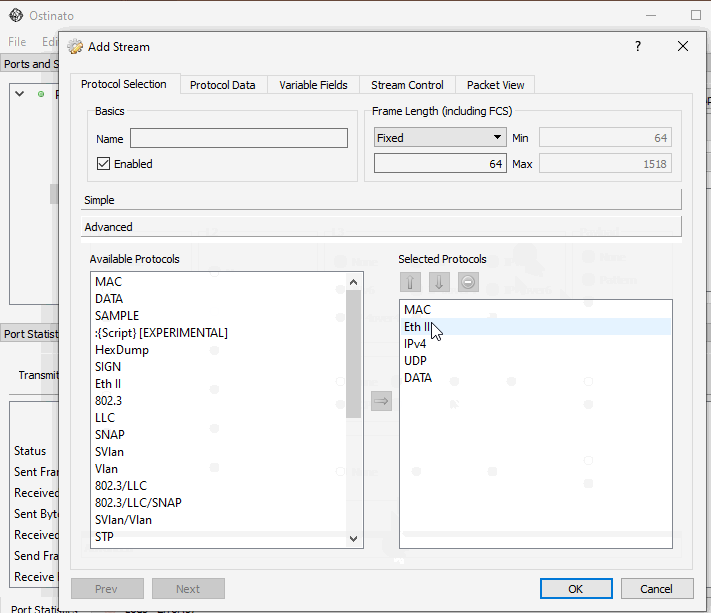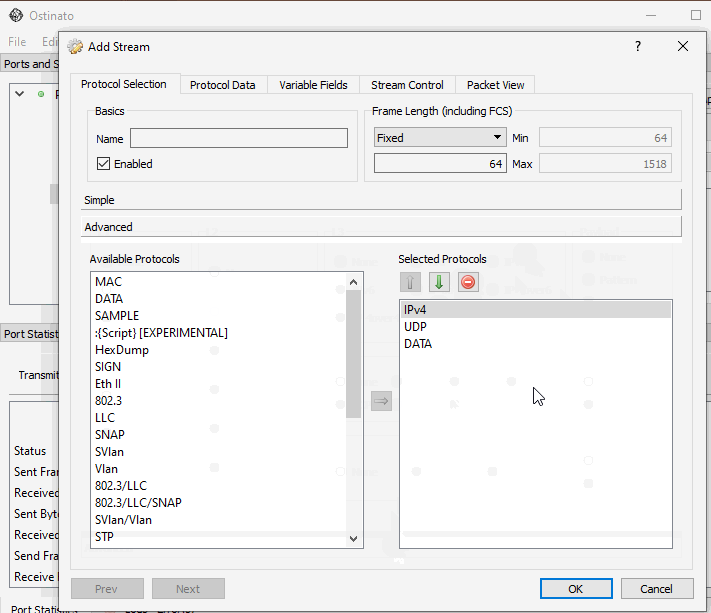
If the virtual interface is an ethernet interface, you can create standard ethernet streams.
However, if the virtual interface is an IP interface, you can create a standard Ethernet/IP stream and then using the Advanced Protocol Selection mode, remove the Ethernet header so that the packet starts directly from the IP header.
What about the protocol headers?
The Linux virtual interface will take care of adding the protocol specific headers for you. That’s why you just need to configure an Ethernet or IP stream on the virtual interface.
That’s the beauty of this approach - you can use the same topology and approach for all these protocols that are implemented as Linux Virtual Network Interfaces.
Example: Using MACsec Interface with Ostinato
Let’s look at a practical example using MACsec.
-
Create MACsec Interface
ip link add link eth0 macsec0 type macsecip link set macsec0 up -
Configure MACsec Parameters
ip macsec add macsec0 tx sa 0 pn 1 on key 01 0123456789abcdef0123456789abcdefip macsec add macsec0 rx address <peer-mac-address> port 1 sa 0 pn 1 on key 01 0123456789abcdef0123456789abcdef - Configure Ostinato Stream
- Select the
macsec0interface in the Ostinato GUI - Create a standard Ethernet stream - don’t worry about macsec header, the macsec interface will add it
- Set up rest of the stream protocols and rates as needed
- Select the
-
Create and configure the peer If the DUT is the macsec peer, you can proceed to running the test. However, if the DUT is a middle box, you must create a similar MACsec interface on the peer side.
- Run Test
- Start traffic generation
- Monitor interface statistics
- Verify MACsec encryption/decryption
- Check for any errors
Extending to Other Protocols
The same topology and approach can be used for other protocols implemented as virtual interfaces. Here are some key considerations:
- Protocol-specific Requirements
- Some protocols may require specific kernel modules
- Each protocol has specific configuration parameters (check the man page for
ip link) - Each protocol has their own specific headers
- Common Testing Parameters
- Frame size/MTU
- Traffic rate
- Protocol-specific fields
- Error conditions
- Monitoring and Validation
- Interface statistics
- Protocol-specific counters
- Error rates
- Performance metrics
Open-source projects
Beyond the Linux kernel, there are also many open source projects that implement other protocols and applications as virtual interfaces. Some examples are -
- StrongSWAN - IPsec
- UERANSIM - 5G RAN
- srsRAN - 4G/5G RAN
- Wireguard - VPN
- and others
These could also be used along with Ostinato with a similar approach.
