What is DMVPN?
DMVPN (Dynamic Multipoint VPN) is a Cisco-developed solution that creates a secure, scalable overlay network. It combines the benefits of IPSec VPN and mGRE (Multipoint Generic Routing Encapsulation) tunnels.
DMVPN solves several challenges in traditional VPN deployments:
- Dynamic tunnel establishment: Tunnels are created on-demand between sites
- Spoke-to-spoke communication: Direct communication between branch offices without going through the hub
- Zero-touch deployment: New sites can join the network without manual configuration
- Scalability: Supports hundreds or thousands of sites with minimal configuration
A typical DMVPN network has three components:
- Hub: The central router that maintains the control plane
- Spokes: Branch office routers that connect to the hub
- NHRP (Next Hop Resolution Protocol): Manages the dynamic mapping of tunnel endpoints
DMVPN operates in three phases:
- Phase 1: All traffic flows through the hub (hub-and-spoke)
- Phase 2: Direct spoke-to-spoke tunnels with hub routing
- Phase 3: Direct spoke-to-spoke tunnels with spoke routing
This architecture makes DMVPN ideal for large-scale enterprise networks. It provides flexibility, scalability, and efficient bandwidth utilization.
Here’s a DMVPN topology (picture courtesy Cisco)
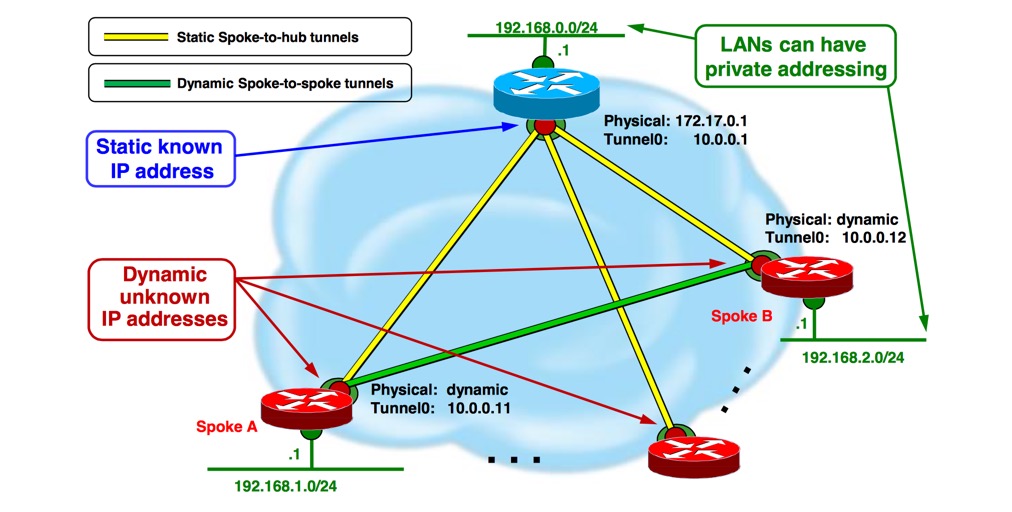
Test topology
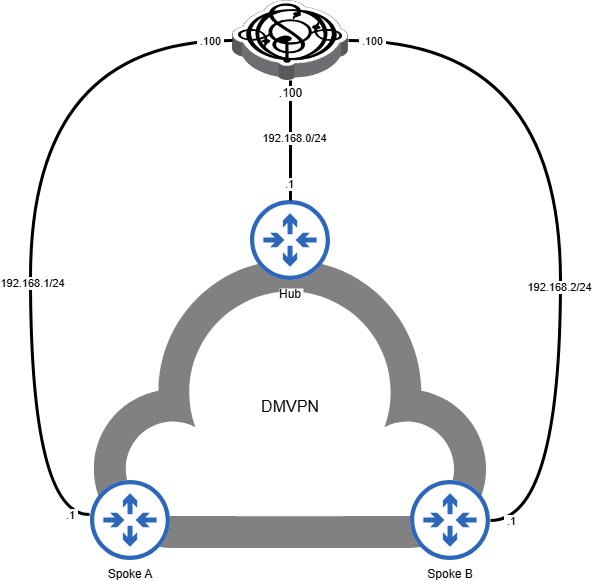
To test DMVPN, we extend the above topology by connecting Ostinato to the LAN side of the hub and spoke routers.
If you are labbing this, you can use a single Ostinato node with multiple links as shown below - this will make it easier to see all traffic in a single GUI with all 3 ports.
If you are testing this in production or a geographically distributed environment, you can use multiple Ostinato drone agents as shown below. All the ostinato drone agents are managed by a single Ostinato GUI controller over a out-of-band management network.
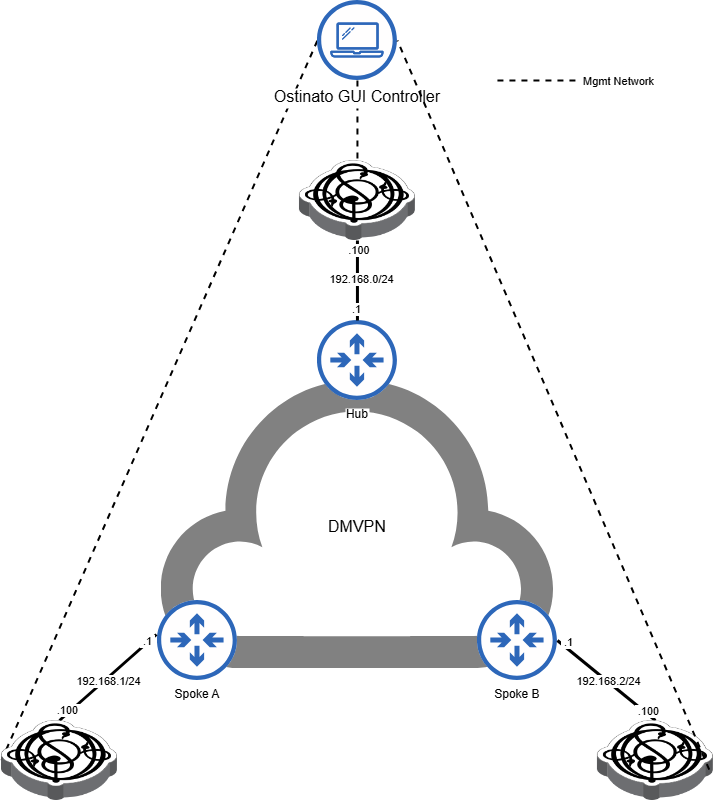
If you don’t have out-of-band management access to the hosts running the drone agents, you can run both the Ostinato GUI controller and the drone agent on each node - you will have 3 Ostinato GUI windows - one per node.
Test Configuration
Since the Ostinato node(s) are connected to the LAN side of the routers, we don’t need to worry about the WAN side of the DMVPN and the overlay/underlay IP addresses.
Configure an emulated device on each of those ports on the Ostinato side. Here’s an example for the Ostinato ethernet port connected to Spoke A -
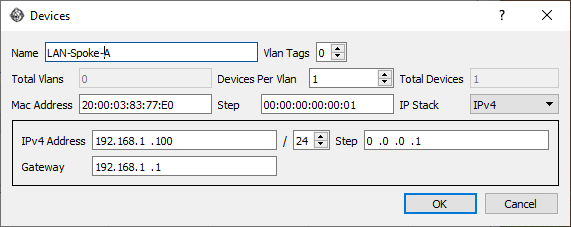
Configure similar devices on the other Ostinato ports/nodes with the appropriate IP addresses.
Then create IP traffic streams on each port towards the Hub and other Spoke. e.g. for the Ostinato ethernet port connected to Spoke A, create two streams -
- Stream 1 (Spoke A to Hub):
192.168.1.100–>192.168.0.100 - Stream 2 (Spoke A to Spoke B):
192.168.1.100–>192.168.2.100
You can create similar streams for other spoke-spoke and spoke-hub pairs.
To test the DMVPN, send the traffic streams and verify that the DMVPN is working correctly - use the Ostinato port stats window and monitor the traffic rates on the TX and RX ports -
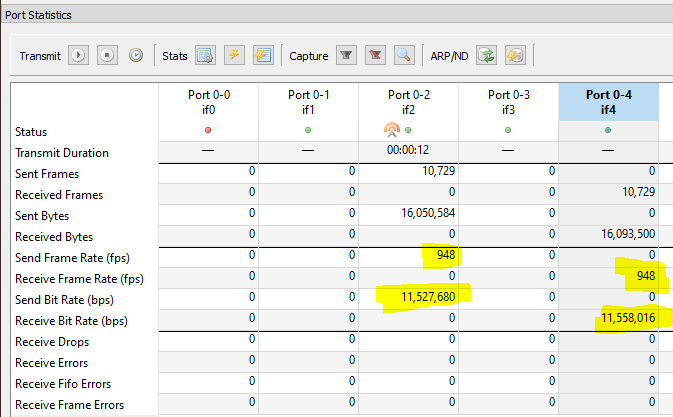
You can also use per-stream statistics if exact packet loss, latency/jitter is of interest.
Test Scenarios
Here are some important scenarios to test your DMVPN setup:
- Initial Tunnel Establishment
- Verify direct spoke-to-spoke tunnel creation
- Measure tunnel setup time
- Check packet loss during tunnel establishment
- Verify NHRP registration and resolution
- Monitor IPsec SA establishment
- Phase Transition Testing
- Test Phase 1 hub-and-spoke operation
- Verify Phase 2 direct tunnel creation
- Validate Phase 3 routing capabilities
- Check NHRP shortcuts and routing table updates
- Failover Testing
- Simulate WAN link failure between spokes
- Verify traffic fallback to hub-and-spoke mode
- Test recovery when direct tunnel is restored
- Monitor NHRP cache timeout behavior
- Performance Testing
- Measure throughput with different packet sizes
- Test with mixed TCP and UDP traffic
- Check latency and jitter using stream statistics
- Scale Testing
- Add multiple spoke sites gradually
- Monitor hub resource utilization
- Test maximum number of concurrent tunnels
- QoS and MTU
- Test with different DSCP markings
- Verify large packets and fragmentation
- Check QoS prioritization across tunnels
- Account for IPsec and GRE overhead in MTU
