Introduction
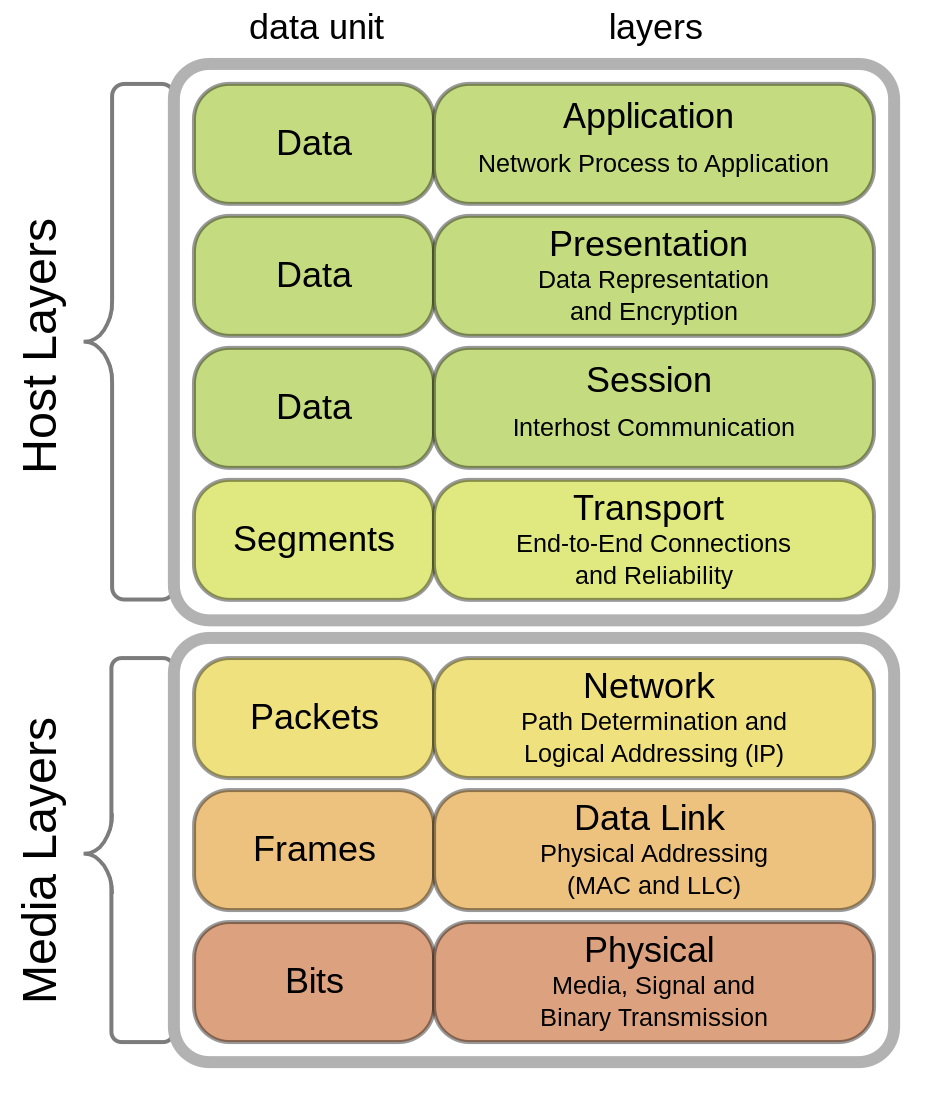
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are protocols used in computer networking to facilitate communication between devices over the Internet or local networks. They operate at the transport layer (Layer 4) of the OSI reference model and employ distinct strategies for managing packet delivery across networks.
The Conversation Modes of TCP and UDP
Imagine applications on different devices are people communicating important information. TCP and UDP act like different modes of communication ensuring information gets transmitted from either end. Here is a deeper dive into their approaches:
What is TCP (Transmission Control Protocol)?
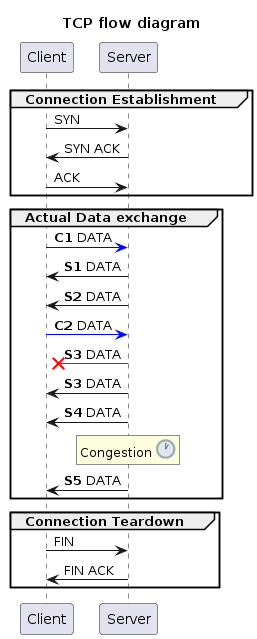
TCP is like a formal meeting - reliable, ordered.

Connection-Oriented: TCP establishes a connection between sender and receiver like a handshake before information exchange begins. This three-way handshake ensures both parties are ready and prepared to communicate.
Sequenced Communication: TCP sends data packets in a specific order, much like following an agenda during a meeting. Each data segment is numbered, and the receiver acknowledges receipt in the correct sequence. This ensures no information is missed or delivered out of order.
Error Checking and Retries: Similar to reviewing meeting minutes for accuracy, TCP verifies data integrity using checksums, mathematical calculations that detect errors. Corrupted packets are automatically resent until acknowledged correctly. This meticulous approach guarantees reliable delivery but can be slower.
Congestion Control: TCP adapts to network conditions, just like a meeting might pause or reschedule if discussions become overwhelming. It dynamically adjusts the data flow to avoid overloading the network and causing congestion.
Advantages of TCP
- Ensures reliable and ordered delivery of data.
- Detects and corrects errors through checksums and retransmissions.
- Ideal for applications requiring high data integrity (e.g., web browsing, emails, file transfers).
Disadvantages of TCP
- Slower transmission due to connection establishment, error checking, and congestion control overhead.
- Consumes more resources for connection management.
What is UDP (User Datagram Protocol)?
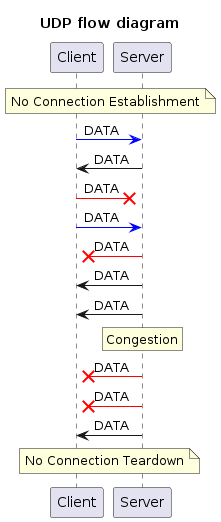
UDP is like a casual conversation - fast and unordered.

Connectionless: Unlike TCP, UDP does not establish a formal connection beforehand. It is more like a casual conversation where messages (datagrams) are sent spontaneously without prior agreement.
Streamlined Communication: UDP prioritizes speed over order. Datagrams are sent independently, and their arrival order is not guaranteed. This is suitable for situations where slight reordering or missing messages are acceptable.
No Guarantees: UDP does not ensure every message is received or arrives in order. Similar to a casual chat where you might miss a word or two, some datagrams might get lost or arrive out of sequence.
Advantages of UDP
- Faster transmission with lower latency due to the lack of connection overhead.
- Reduced resource usage due to the simpler protocol.
- Well-suited for real-time applications (e.g., online gaming, video/audio streaming, VoIP calls).
Disadvantages of UDP:
- No guaranteed delivery or order of data.
- No built-in error correction mechanisms.
- Less reliable for data integrity-sensitive applications.
Choosing the Right Communication Mode
Reliable Communication: Use TCP for applications that require guaranteed delivery and order, like sending important files or emails where errors are unacceptable.
Real-Time Interaction: Use UDP for applications that prioritize speed over perfect delivery, such as online gaming or live streaming where slight delays or occasional missing data can be tolerated.
Security Considerations
TCP with Secure Sockets: TCP can be secured with technologies like SSL/TLS, which act like encrypted emails protecting the message content during transmission (used for online banking or secure email).
Securing UDP Yourself: UDP offers no built-in security. If needed, additional encryption methods must be implemented, similar to using a secret code during a casual conversation.
Real-World Examples
Emails rely on TCP to ensure reliable delivery of messages and attachments, even if it takes a bit longer.
VoIP calls leverage UDP to prioritize real-time voice chat, even if there might be occasional dropped packets causing brief audio glitches or distortions. Apart from voice/video applications, UDP finds usage in service provider networks where the underlay is a (layer 3) IP network. We shall talk about this in detail in a future guides post.
A note on Ostinato TCP traffic generation
Ostinato generates raw TCP traffic, bypassing features like state management and error handling. It does not track sequence numbers or resend lost packets.
This is a guest post by Tanu Vishwanath - a dataplane network engineer with 20 years of industry experience
